<%NUMBERING1%>.<%NUMBERING2%>.<%NUMBERING3%> PRTG Manual: User Access Rights
The default administrator can use the PRTG installation as the only user or can create an unlimited number of users. Users are organized in an unlimited number of user groups. Access rights for each individual object in your PRTG device tree can be given separately for each user group (except for sensor channels). Access rights to objects can also be inherited.
In addition, every single user has specific rights: There are administrator users, read/write users, and read only users. You can define these settings in System Administration—User Accounts. With these tools, you can create a rights management that allows you to specify exactly what users will be able to see and edit.
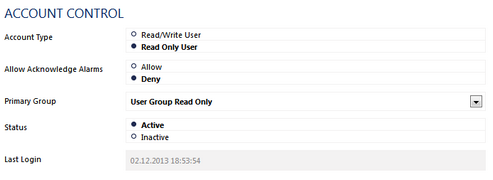
User Rights in User Account Settings
Individual user rights in combination with access rights of the group(s) they belong to conduct the access rights to certain objects in the device tree. This means that group membership particularly controls what a user is allowed to do and which objects the user will see when logged in.
The actual access rights for each object in the device tree can be defined in an object's settings. You can define different access rights for all sensors, devices, groups, or probes via the corresponding Context Menus or in the Object Settings.
The following classes of access rights for objects are available in hierarchical order as they can be given to user groups (lowest rights to highest rights):
- None: The object will not be displayed to the users of the group; no logs, no tickets, no alarms regarding this object will appear.
- Read: Only monitoring results can be seen.
- Write: Reviewing monitoring results and editing settings is allowed. In addition, objects can be added to and deleted from the device tree.
- Full: Reviewing monitoring results, editing settings, and editing access rights is allowed. In addition, objects can be added to and deleted from the device tree.
- Admin rights: If a user group has administrator rights, all options are available, including creating users, creating user groups, and deleting objects from the device tree. Access restrictions to objects cannot be set for this type of user group.
Note: Access rights that are defined locally on an object, for example, on a device, override inherited rights. On a certain object, the highest directly set access right applies for a user group. If there is no access right set directly on an object, the next higher object level will be checked for access rights. This process is repeated until defined access rights are found to be inherited or there is no higher object level.
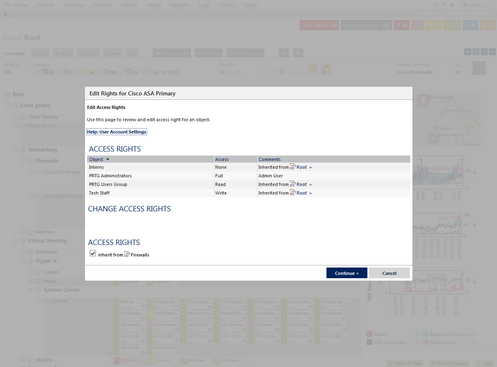
Different Access Rights for a Firewall in the Device Tree Depending on User Groups
Please see the table below for which user rights apply when. Column headings show access rights of user groups for objects in the device tree; line headings show the type of user.
Note: Users are either in PRTG user groups or in Active Directory Domain user groups. They cannot be in both. We recommend to use only one type of user group (either PRTG or Active Directory) to minimize your administration effort.
|
|
|
|
|
Read Access |
Read/Write Access |
Full Access |
|
|
|
Read-only rights |
Read-only rights |
Read-only rights |
Admin rights |
|
Read-only rights |
Read/write rights |
Full access |
Admin rights |
- Users in an administrator group have always administrator access rights, no matter of the access rights of an object.
- Read-only users have just read rights, no matter of the access rights of their group, except for users which are members of an administrator group.
- Read/write users in a group with full access to an object have full access rights to this object only.
- If a user is in more than one group, access rights of the user group with the highest rights apply.
- Administrator rights can only be given via the administrator group.
For more information about defining access rights, please see the following sections:
For information about connecting PRTG to an existing Active Directory, please see Active Directory Integration.
Keywords: User Access Rights